
Here I have collected some of my linux experiences bundled in this blog. Hope you guys will enjoy this blog we well like the earlier ones. Thanks a lot, and keep reading. Here it is:
Q1. How to get the version of Linux installed in the system?
Ans:
cat /etc/redhat-release
Q2. How to get the version of Linux Kernel?
Ans:
uname -a
Q3. How to check the current runlevel?
Ans:
$runlevel
Red Hat Linux and Fedora
Red Hat as well as most of its derivatives uses runlevels like this:
- 0 - Halt
- 1 - Single user
- 2 - Not used/User definable
- 3 - Full multi-user, console logins only
- 4 - Not used/User definable
- 5 - Full multi-user, with display manager as well as console logins
- 6 - Reboot
Ref: http://en.wikipedia.org/wiki/Runlevel.
Q4.
Ans:
Q5. How to start the computer in single user mode?
Ans:
a) Type 'single' at the end of the boot line
b) Type 'init 1' at the end of the boot line
Q6. How to boot linux in super user mode?
Ans:
Change the boot loader kernel booting option while starting the kernel just after the boot loader starts.
"init 1" should be passed as the last parameter, and then b to boot with this parameter. Linux will boot in single user mode. In case you want to change the root passwd, this is the time, use the passwd command to change the root passwd.
Q7. What is the equivalent command in HPUX for 'ipconfig -a'?
Ans:
There is no equivalent command of 'ipconfig -a' in HPUX, rather use the following script code in command line:
for lan in $(lanscan | grep lan | awk '{print $5}') ; do
echo $lan
ifconfig $lan
done
Q8.How to configure different services in start-up?
Ans:
'chkconfig' is the command.
Graphically, Red Hat / Fedora Core GUI: system-config-services (and redhat-config-services)
Red Hat/Fedora Core text console services selection tool: /usr/sbin/ntsysv
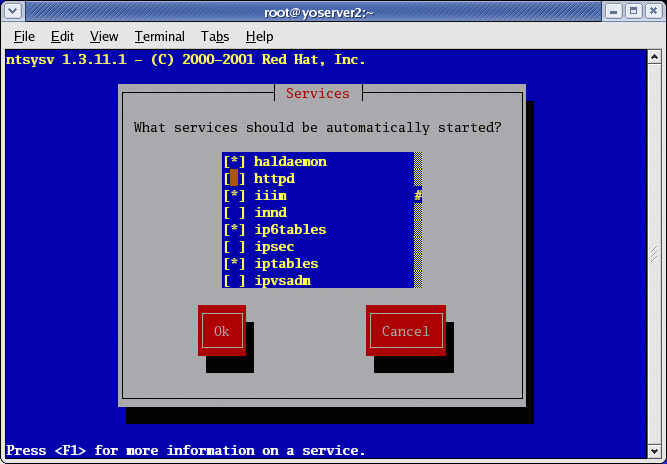
Q9.What Is a core File?
Ans: A core file is created when a program terminates unexpectedly, due to a bug, or a violation of the operating system's or hardware's protection mechanisms. The operating system kills the program and creates a core file that programmers can use to figure out what went wrong. It contains a detailed description of the state that the program was in when it died.
If would like to determine what program a core file came from, use the file command, like this:
$ file core
That will tell you the name of the program that produced the core dump. You may want to write the maintainer(s) of the program, telling them that their program dumped core.
Q10. How To Enable or Disable Core Dumps
Ans: By using the ulimit command in bash, the limit command in tcsh, or the rlimit command in ksh. See the appropriate manual page for details.
This setting affects all programs run from the shell (directly or indirectly), not the whole system.
If you wish to enable or disable core dumping for all processes by default, you can change the default setting in linux/sched.h. Refer to definition of INIT_TASK, and look also in linux/resource.h.
PAM support optimizes the system's environment, including the amount of memory a user is allowed. In some distributions this parameter is configurable in the /etc/security/limits.conf file.
Q11. What are different types of open source licenses?
Ans:
Open source licenses may be broadly categorized into the following types: (1) those that apply no restrictions on the distribution of derivative works (we will call these Non-Protective Licenses because they do not protect the code from being used in non-Open Source applications); and (2) those that do apply such restrictions (we will call these Protective Licenses because they ensure that the code will always remain open/free).
To better appreciate the nature of these licenses, it is helpful to picture software licenses on a continuum based on the rights in copyright extended to the licensee.
Software that has been placed in the public domain is free of all restrictions, all rights under copyright having been granted to the public at large. Licensors of Non-Protective Open Source licenses retain their copyright, but they grant all rights under copyright to the licensee. Licensors of Protective Open Source licenses retain their copyright, grant all rights under copyright to the licensee, but apply at least one restriction, typically that the redistribution of the software, whether modified or unmodified, must be under the same license. Licensors of propriety licenses retain their copyright and only grant a few rights under copyright, typically only the rights to perform and display. The BSD license is an example of a Non-Protective Open Source license and the GNU General Public License is an example of a Protective Open Source license.
List of some open source licensed products::
Non-Protective Open Source licenses include: Academic Free License v.1.2; Apache Software License v.1.1; Artistic; Attribution Assurance license; BSD License; Eiffel Forum License; Intel Open Source License for CDSA/CSSM Implementation; MIT License; Open Group Test Suite License; Q Public License v.1.0; Sleepycat License; Sun Industry Standards Source License; University of Illinois/NCSA Open Source License; Vovida Software License v.1.0; W3C Software Notice and License; X.Net, Inc. License; zlib/libpng License; and Zope Public License v.2.0.
Protective Open Source licenses include: Apple Public Source License v.1.2; Artistic License; Common Public License v.1.0; GNU General Public License v.2.0; GNU Lesser General Public License v.2.1; IBM Public License v.1.0; Jabber Open Source License v.1.0; MITRE Collaborative Virtual Workspace License; Motosoto Open Source License v.0.9.1; Mozilla Public License v.1.0 and v.1.1; Nethack General Public License; Noika Open Source License v.1.0a; OCLC Research Public License v.1.0; Open Software License v.1.1; Python License; Python Software Foundation License v.2.1.1; Ricoh Source Code Public License v.1.0; and Sun Public License v.1.0.
Q12:
Here is a nice link which talks about the Command-line Calculator in Linux
Ans:
http://linux.byexamples.com/archives/42/command-line-calculator-bc/
Q13: What is copyleft?
Ans:
Copyleft is a great license originally designed for software which can be applied to images, text, pictures and any other work for that matter. The license says the work is free and must remain free. You can do what you want with the work as long as it remains in the commons. You can not take a Copyleft picture and put it on a website that has a copyright notice restricting others from freely using the picture, but you can use it if you are using Copyleft yourself.
Copyleft is a very good idea for music also. Most so-called "samples" used to create modern music are owned by large corporations who insist you buy their music using a polluting, non-sustainable media called DVD discs. Copyleft music can be distributed freely, meaning people will promote your bands music to the millions at no cost to you.
No comments:
Post a Comment